Risk Assessment
Identifying and knowing the location, scope
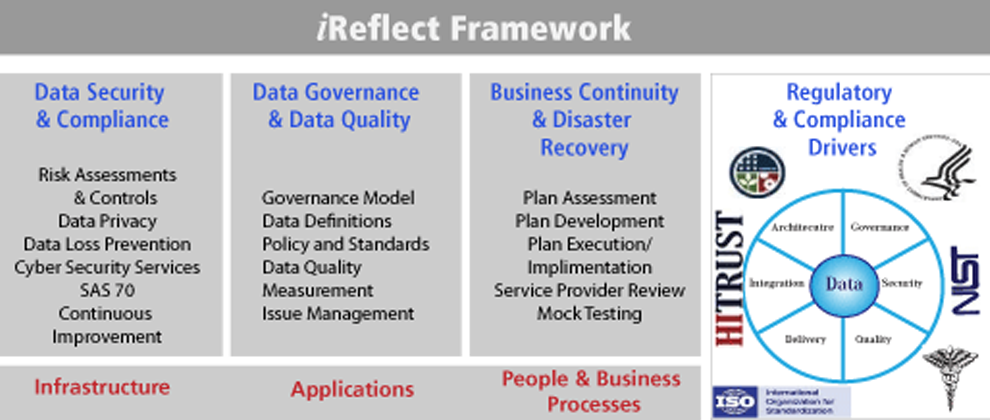
There are a wide variety of commonly used risk assessment methodologies including NIST, and ISO-27002. While “quantitative” risk assessments are alluring - the challenges to establishing probabilities and calculating impact costs across multiple criteria drive us to favor “qualitative’ risk assessment.
Critical to good risk assessment practice is tightly defining the scope and context of the risk assessment. We favor defining the scope formally in a Security Data Flow Diagram (SDFD) and then conducting the risk assessment against the SDFD leveraging a process/info based risk approach at each point in the SDFD. This approach shortens the time to conduct the risk assessment by more tightly focusing the risk assessment sessions and also significantly decreases the possibility of a key risk being missed.
